The most dangerous line in the EDPB's new blockchain guidelines isn't buried in technical jargon—it's explicitly stating that regulators may order the deletion of entire chains that can't accommodate data erasure requests.
The EDPB’s Blockchain Guidelines: What’s Really At Stake
Last month, the European Data Protection Board (EDPB) released Guidelines 02/2025 on processing personal data via blockchain technologies. These guidelines, open for public consultation until June 30, 2025, aim to align blockchain practices with the EU's GDPR requirements.
The guidelines establish several key provisions for blockchain operators in the EU. They clarify that public keys linked to natural persons constitute personal data under GDPR, recommend Data Protection Impact Assessments (DPIAs) before deploying blockchain solutions, and express a clear preference for permissioned blockchains over public infrastructure. Most controversially, they include a provision that could allow regulators to order the complete deletion of blockchain data—or even entire blockchains—if GDPR compliance cannot otherwise be achieved.
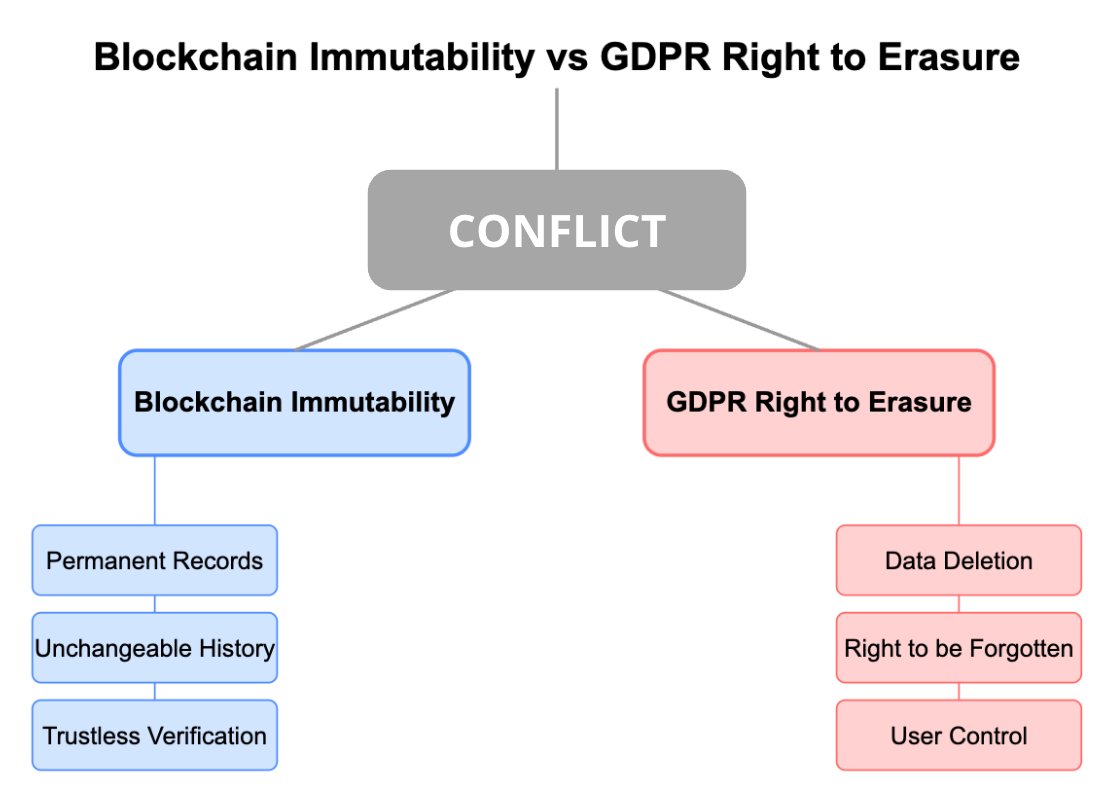
At the heart of this conflict is a fundamental contradiction: blockchain's immutable design versus GDPR's right to erasure. When users request their personal data be deleted under GDPR's "right to be forgotten," blockchain's permanent, unalterable ledger creates an impossible compliance scenario.
Most alarming is what some are calling the "blockchain kill switch" — the EDPB explicitly states that if a blockchain cannot accommodate GDPR rights like erasure, regulators may order the deletion of the entire chain.
What's striking is the irony: In the name of "protecting users," regulators are preparing to destroy the very technology that gives users unprecedented power over their digital lives. The EU claims to champion user rights while simultaneously undermining the most promising path to true digital self-sovereignty.
These guidelines aren't just technical inconveniences—they represent an existential threat to public blockchain infrastructure in Europe. And they reveal a fundamental misunderstanding about the relationship between privacy, freedom, and decentralization.
The Privacy Paradox: When Protection Becomes Control
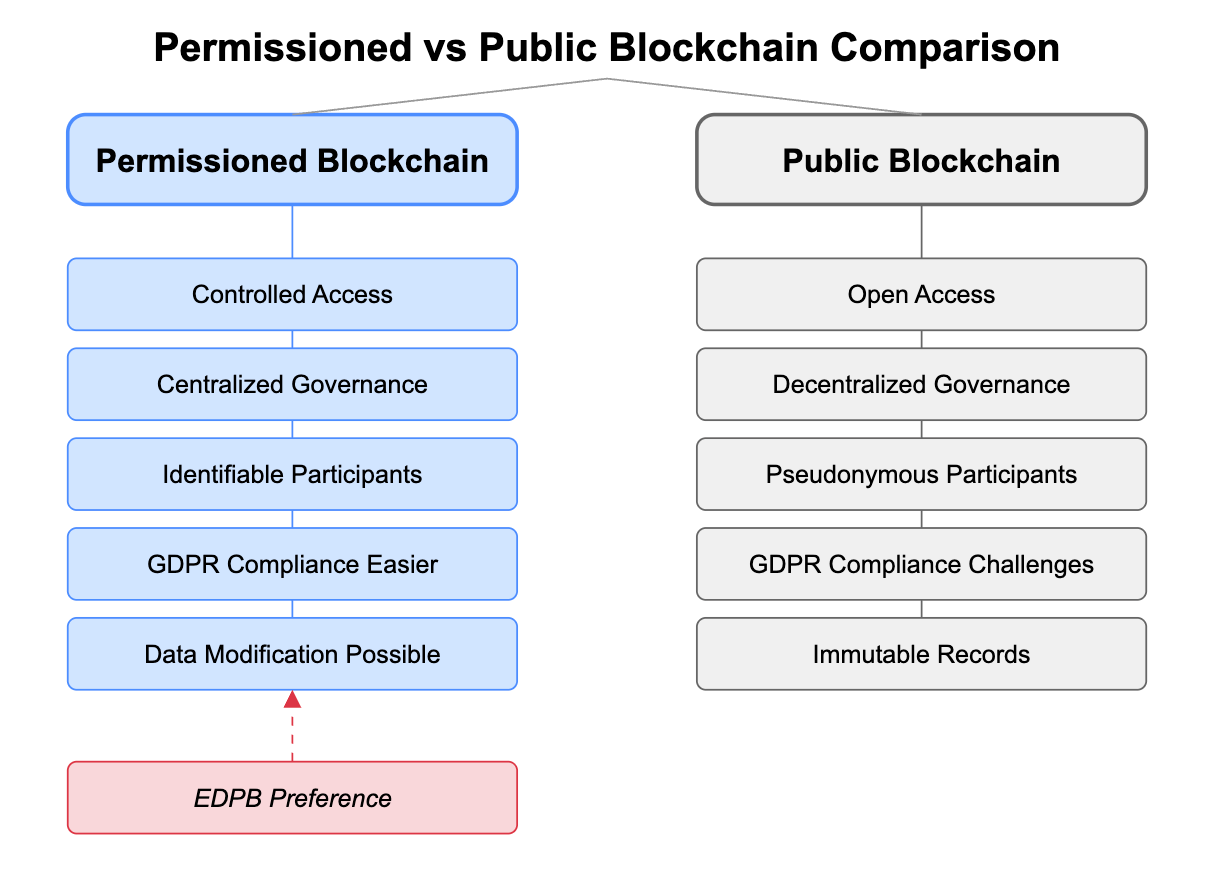
The EDPB guidance exemplifies a broader regulatory pattern: applying top-down regulatory frameworks to bottom-up, decentralized technologies. The guidelines recommend permissioned blockchains, effectively endorsing systems where access is managed by specific entities or gatekeepers. This stands in stark contrast to the foundational intent of public blockchains, where decentralization and user autonomy are paramount.
James Smith, Special Projects Lead at the Ethereum Foundation, summed up industry apprehension: "Without significant pushback, we’re facing a regulatory framework that fundamentally misunderstands decentralized technology". Other prominent stakeholders, such as the European Crypto Initiative (EUCI), have cautioned that such an approach could chill innovation within the European blockchain ecosystem.
Consider this excerpt from the guidelines: "...permissioned blockchains are generally favored from a data protection perspective." In plain language: the EU prefers the blockchain equivalent of walled gardens. Systems where gatekeepers control who can participate and how data flows. This fundamentally contradicts the core value proposition of blockchain technology—removing intermediaries between users and their data.
The economic implications are stark. Last week in my DMs on Crypto Twitter, a DeFi founder told me they're already planning to relocate their protocol outside the EU. "We can't build with this regulatory uncertainty," they explained. "If we can't guarantee our infrastructure won't be forced offline by a deletion request, how can we attract developers or users?"
They're not alone. Since the draft guidelines leaked, there's been a noticeable chill in European-based protocol deployments while competing hubs in Dubai and Singapore have seen increases.
What regulators fail to understand is that privacy and decentralization can be complementary, not contradictory. Public blockchains don't inherently violate privacy—they simply require different privacy-preserving approaches than traditional databases.
The EDPB's approach creates a false choice between privacy and decentralization. By favoring permissioned systems, they're actually reducing users' technical sovereignty—their freedom to choose truly censorship-resistant, self-custodial systems. Instead of empowering users, they're empowering gatekeepers.
Similarly, the EU's top-down regulation threatens to suffocate genuine innovation in privacy-preserving technologies. By trying to force "delete buttons" onto systems explicitly designed not to have them, regulators miss the much more interesting developments in zero-knowledge proofs, off-chain data storage, and privacy-focused Layer 2 solutions.
The irony is palpable: in trying to protect users' privacy, the EU risks eliminating the very tools that could give users unprecedented privacy with self-sovereignty. It's protection that becomes control—safety at the cost of freedom.
At the same time, the technical reality is a bit more nuanced: public blockchains do not necessarily violate user privacy by design. Instead, they require different strategies for privacy preservation than conventional, centralized databases. The imposition of GDPR-style erasure as a universal condition risks overlooking the steady advancements in privacy-preserving blockchain technology, such as zero-knowledge proofs (ZKPs) and minimal on-chain identity linkage.
The Sovereign Data Strategy: Building Privacy Without Sacrificing Freedom
While the EDPB's concern for user privacy is legitimate, their approach fails to recognize how blockchain technology fundamentally changes the relationship between users and their data. Instead of forcing traditional data protection frameworks onto blockchain architecture, a more effective approach would preserve both privacy and decentralization through thoughtful design.
As stated earlier, the deadline for public consultation on these guidelines is June 30, 2025. That gives blockchain projects just over a month to adapt, respond, or relocate. But rather than panicking, there's a strategic path forward that preserves both privacy and decentralization.
Drawing from industry best practices, I've developed a structured framework that enables projects to maintain sovereignty while addressing legitimate privacy concerns. The foundation of this approach is proactive design rather than reactive compliance.
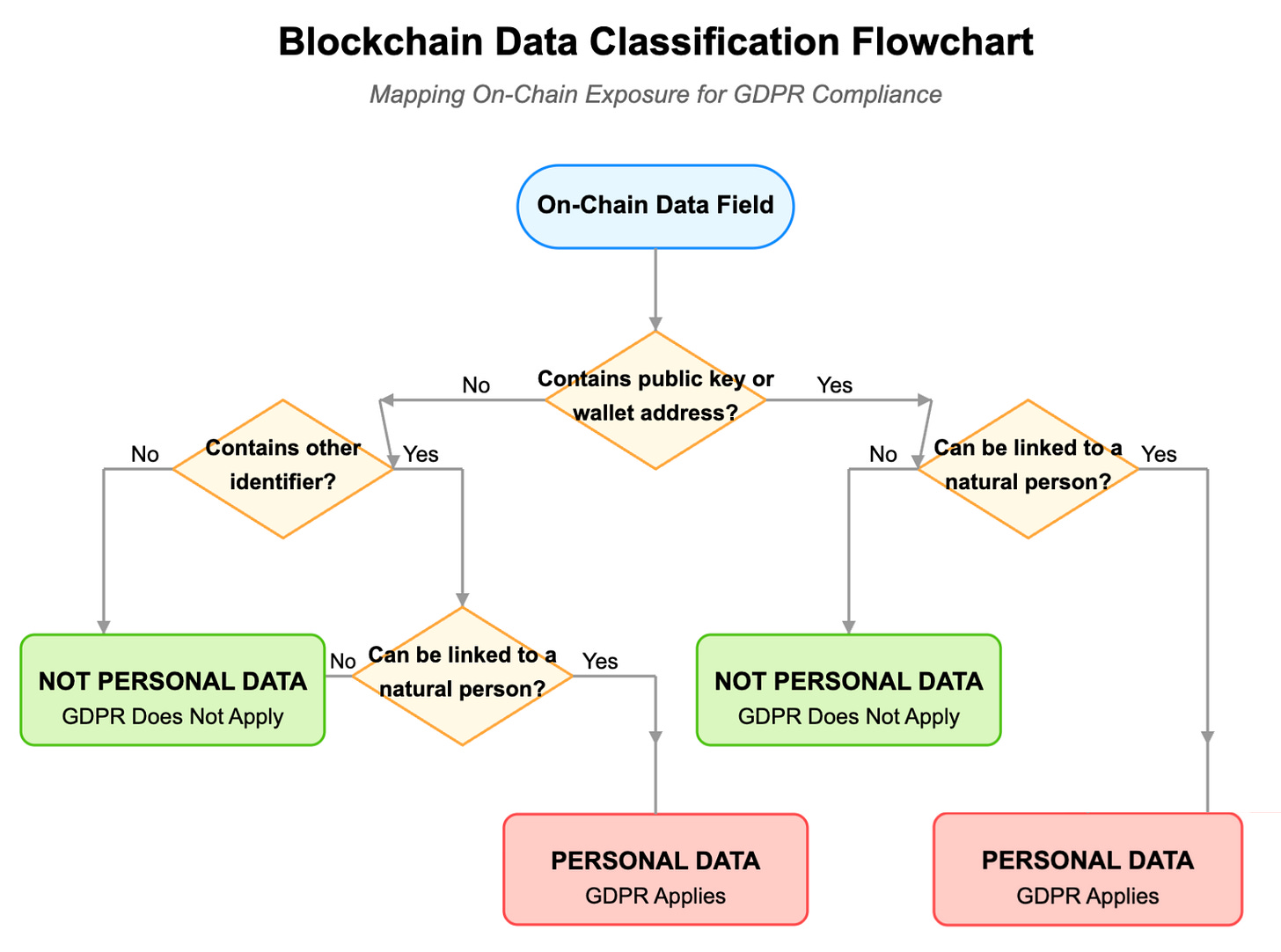
Step 1. Map On-Chain Exposure
The first critical task is identifying where your protocol actually processes personal data. The EDPB explicitly states that public keys linked to natural persons are considered personal data under GDPR.
Project teams should audit their protocols to identify precisely where (if at all) personal data is processed or stored on-chain. Often, much of the data developers believe to be personally identifiable can, in fact, remain off-chain with appropriate architectural choices.
Teams should examine their transaction patterns and identify exactly what user information is being stored where. Look at which contract functions collect addresses, check if they're associated with other personal identifiers, and determine which interactions would fall under GDPR's scope.
Most protocols unconsciously put more data on-chain than they need to—not because it's necessary, but because it's the path of least resistance.
Map every data field your protocol stores on-chain and ask: "Could this conceivably identify a natural person?" If yes, consider alternatives.
Step 2. Privacy by Design
The key to effective blockchain compliance isn't complex—it's architectural. The most successful implementations I've studied separate identity data from transactional data as a foundational design principle rather than trying to retrofit privacy after the fact.
Privacy by Design doesn't mean abandoning public blockchains. It means being intentional about data storage locations:
Transactional data (e.g., transfer amounts, contract interactions, timestamps) is recorded on-chain, as required for network integrity and security.
Direct identity data (email addresses, real names, user profiles) should remain off-chain or be handled through cryptographic techniques that limit access and ensure user control.
Linkage minimization: The connection between blockchain addresses and real-world identities must be carefully limited.
While explicit identity data is rarely stored on-chain, users can still be deanonymized through on-chain activity analysis. Third-party analytics platforms like Arkham and DeBank, and public registries like Ethereum Name Service (ENS), can match wallet addresses to real identities or social profiles—especially if users voluntarily "dox themselves" by linking their wallets to public accounts or identifiers.
To strengthen privacy, projects and users should:
Limit voluntary disclosures (such as publishing an ENS name linked to a wallet containing sensitive activity).
Design and adopt architectures that minimize the creation of persistent, cross-referenceable records.
Employ privacy-enhancing tools such as mixers, zero-knowledge proofs, or account abstraction to obscure on-chain linkages.
Ensuring true privacy in decentralized systems thus depends less on the avoidance of explicit personal data, and more on an architectural and operational approach that resists the increasingly sophisticated deanonymization methods available in the Web3 ecosystem.
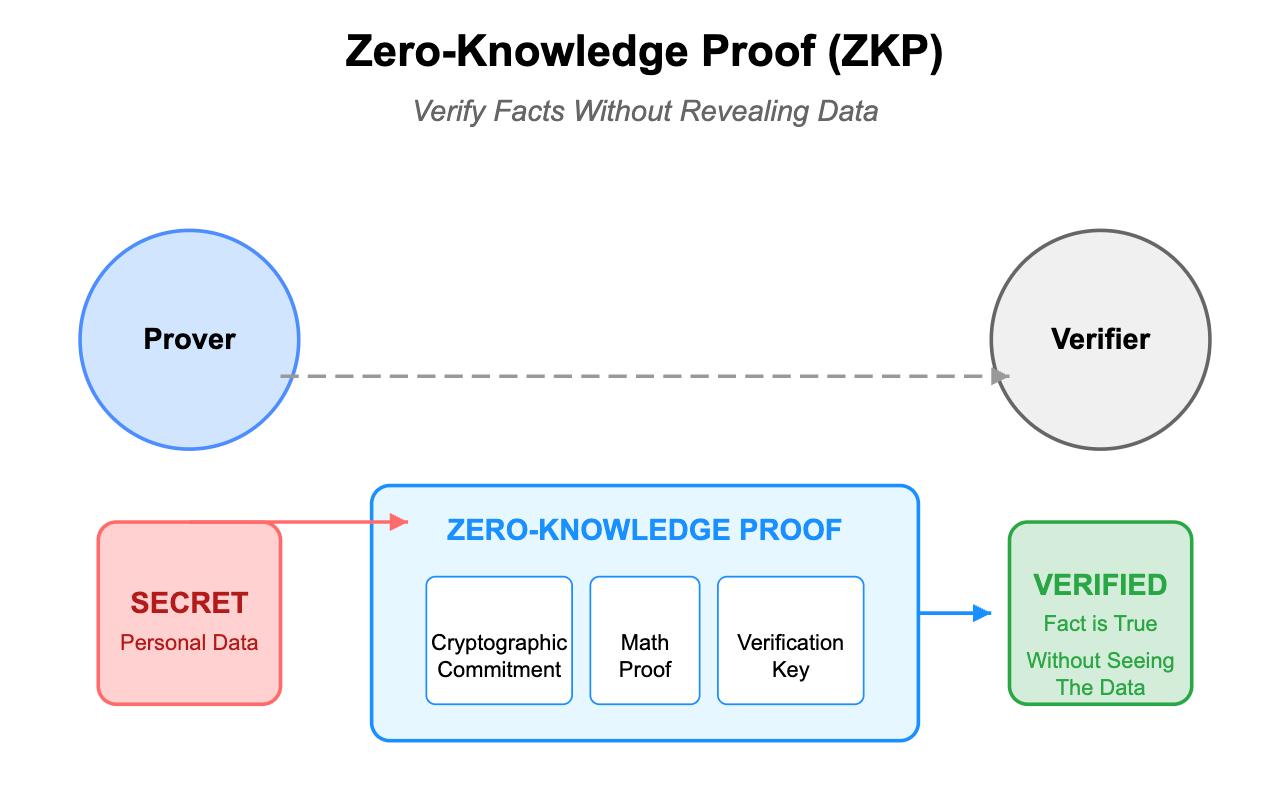
Step 3. Use Zero-Knowledge Infrastructure
Zero-knowledge proofs (ZKPs) are some of the most powerful tools in the blockchain privacy-preserving arsenal. They allow proving facts without revealing the underlying data.
Protocols like zkSync, Privado Id (ex-Polygon ID), and Iden3 have made notable advances, enabling functions such as private transaction verification and anonymous voting without direct personal data storage.
For GDPR compliance, ZK proofs offer a compelling solution: you can't be forced to delete what you never stored in the first place.
Step 4. Create Geographic (and Legal) Resilience
The blunt reality is that regulatory environments vary. Strategic geographic distribution provides crucial resilience against overzealous regulation.
This doesn't mean abandoning Europe—it means thoughtful architecture that respects the global nature of blockchain.
A multi-region approach might include:
Development teams in privacy-friendly jurisdictions
Node infrastructure across multiple continents
Legal entities structured for regulatory optionality
User education about jurisdiction and privacy implications
Step 5. Participate in the Consultation
The EDPB guidelines remain open for public feedback until June 30th. This isn't merely a formality—it's an opportunity to shape policy.
Groups like the European Crypto Initiative and Web3PrivacyNow are coordinating industry responses, but individual projects can also submit evidence-based feedback.
Concrete use cases showing privacy-preserving innovations have significantly more impact than general objections. Regulators respond to specific examples showing how decentralized systems can enhance privacy while preserving user autonomy.
Beyond Regulation: Toward User-Controlled Privacy
The EU's blockchain data guidelines represent a flawed attempt to protect users by limiting their technological options. True privacy doesn't come from restricting technology—it comes from empowering users with better privacy tools within open systems.
While regulators focus on control mechanisms, the blockchain ecosystem is solving privacy through cryptographic innovation rather than deletion rights . The protocols pioneering sovereign identity solutions and zero -knowledge applications aren't just surviving—they're defining the next wave of adoption precisely because they deliver both immutability and privacy simultaneously, something the EDPB guidelines incorrectly frame as incompatible.
The future of digital privacy is best advanced not by restricting technological experimentation or imposing top-down data control, but by supporting cryptographic innovation to give users real agency over their online identities and activities.
Instead of choosing between privacy and decentralization, regulators and industry should engage in evidence-driven dialogue to develop frameworks that protect both. Protocols that implement privacy-preserving and compliance-friendly architectures will set the example for sustainable blockchain innovation—inside and outside the EU.
- Vincent